The Lacoon Mobile Threat Management Platform offers powerful cloud-based analytics and a lightweight device agent allowing enterprises to easily manage and mitigate the mobile security risks of bring your own device (BYOD) and other mobility initiatives.
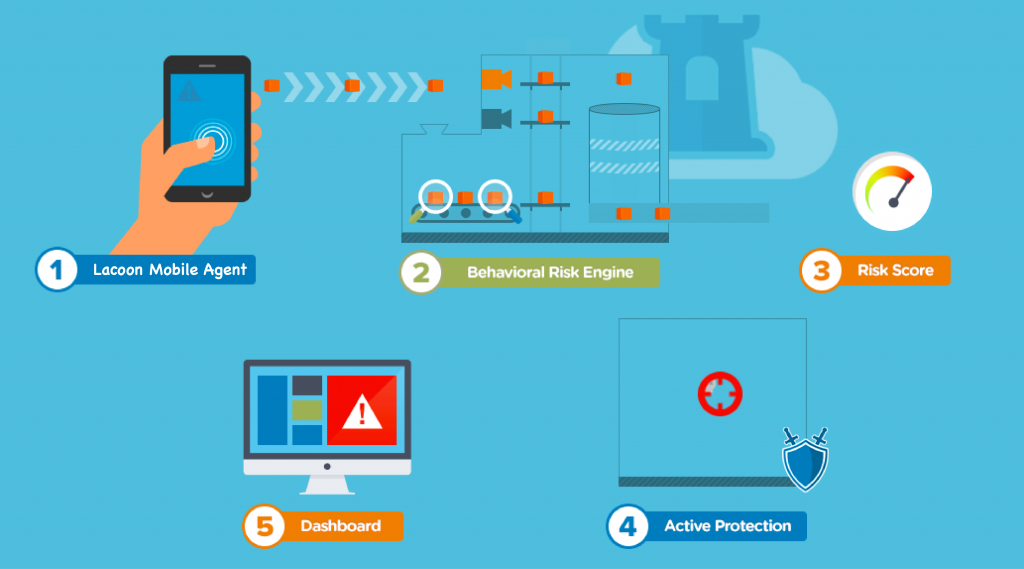
1: Lacoon Mobile Agent
Users download the Lacoon Mobile Agent to start protecting their activity. The non-invasive agent runs in the background with no impact to the user’s experience. If the device is attacked or a user downloads a malicious app, Lacoon will notify them and the enterprise’s IT department and provide instructions on how to eliminate the infection. Note: the solution does not look at or collect any personal information. Learn more about how we preserve mobile user privacy.
2: Behavioral Risk Engine
The Lacoon Mobile Agent sends key information, such as new and unknown apps installed on the device, configurations, logs and events, to the Mobile Threat Management Platform’s Behavioral Risk Engine (BRE) in the cloud for analysis. The BRE uses a number of patent-pending, proprietary techniques to identify vulnerabilities and threats, including:
- Advanced Behavioral Application Analysis – to identify suspicious patterns and application behaviors over time; it may sandbox an application in a mobile device emulator to understand exactly how it interacts with specific device types and the risks it poses.
- On-device and Network Event Anomaly Detection – to identify malicious command and control behaviors and data leakage by unknown malware through the identification of patterns that would otherwise evade detection.
- Real-Time Risk Assessments – to identify changes in configurations or device state that could indicate the exploitation of a vulnerability.
3: Real-Time Risk Score
The BRE assigns a real-time risk score to each device, which is dynamically adjusted according to findings from ongoing assessments. These risk scores are used to determine how traffic from that device should be handled, based on pre-defined risk thresholds and policies set by administrators.
4: Active Protection
High risks typically trigger Active Protection methods, which are pre-defined by the enterprise. Lacoon offers a range of sophisticated options to remediate attacks including:
- On-Device – users receive instructions on how to eliminate malware and malicious applications with just a few clicks.
- In- Network – traffic can be rerouted to the Lacoon Mobile Threat Management Platform’s Cloud Gateway to dynamically activate a VPN to keep communications private or block attack traffic to prevent it ‘calling home’ or stealing data to contain the threat.
- MDM/NAC Integration – access privileges can be adjusted to enable dynamic, risk-based policy enforcement.
5: Dashboard
The Lacoon Mobile Threat Management Platform’s Dashboard gives administrators full visibility and control, with the ability to conduct detailed investigations and forensics to ensure consistent mobile security enforcement.
User Privacy: To learn more about how the Lacoon Mobile Threat Management Platform protects user privacy, please read our FAQ.
